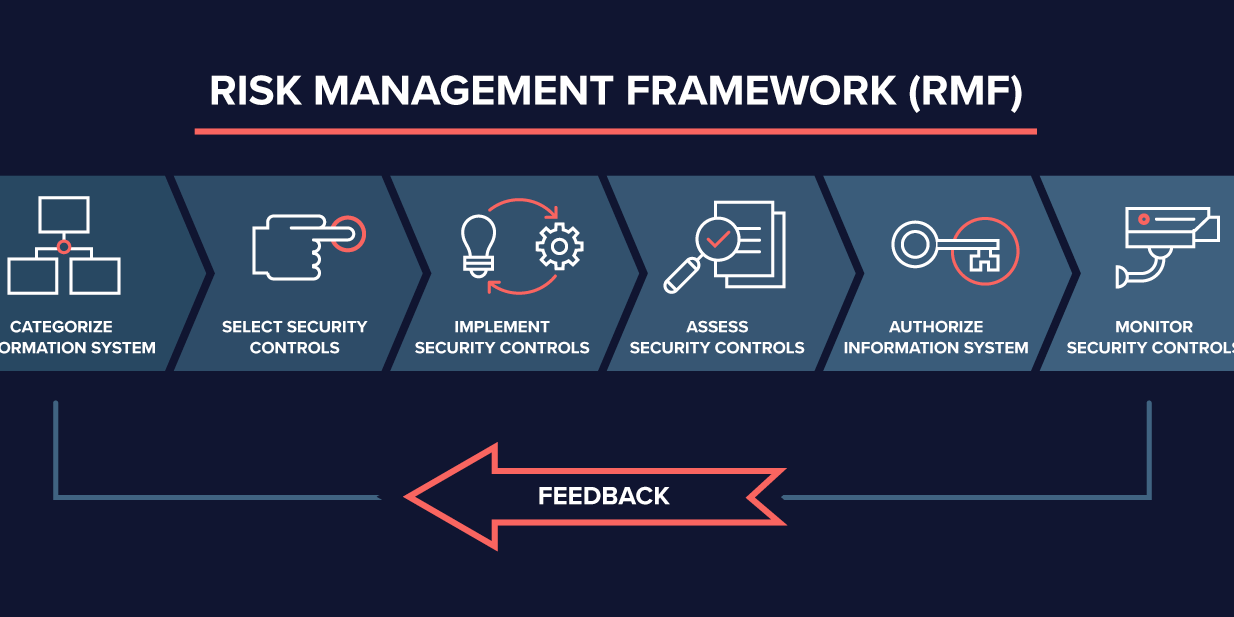
In this four part podcast series, CSIAC subject matter experts (SMEs) conduct a roundtable discussion of the first step of the Risk Management Framework (RMF) process, Categorization, focused specifically on Industrial Control Systems (ICS). The main objective of the categorization phase is to project the potential negative effects upon an organization should certain assets become compromised. This would include the CIA Triad – Confidentiality, Integrity and Availability (CIA) – involving the systems within an enterprise and the associated data those systems may process, store or transmit. Based upon the assessment of the possible risks, certain processes or tasks may be employed to mitigate the potential adverse impacts.
In part one of the RMF Categorization podcast series, the SMEs discuss what a security program is and why it is important. A security program defines the people, processes and technologies used to manage cybersecurity risk to the environment in which your system operates. This document serves as the blueprint for how your system operates and responds to the ever changing threat landscape.
In part two of the RMF Categorization podcast series, the SMEs discuss the process of accurately identifying information types. The identification of the information types establishes the foundation for the system security program. The information types serve as the baseline by which the mission owner as well as the adversary both measure success. Information types allow the system owner to respond to cybersecurity risks by utilizing specified security requirements.
https://www.youtube.com/embed/RhdC3k9sGfs?feature=oembed
In part three of the RMF Categorization podcast series, the SMEs discuss the process of aligning the security objectives. The security objectives provide a common understanding of the impact levels on the information types as well as a common viewpoint of a system compromise and its organizational impact. The security objectives allow the system owner to identify security requirements in order to mitigate and reduce risks to the system.
https://www.youtube.com/embed/okzzq4xo_LE?feature=oembed
In part three of the RMF Categorization podcast series, the SMEs discuss the process of aligning the security objectives. The security objectives provide a common understanding of the impact levels on the information types as well as a common viewpoint of a system compromise and its organizational impact. The security objectives allow the system owner to identify security requirements in order to mitigate and reduce risks to the system.
https://www.youtube.com/embed/okzzq4xo_LE?feature=oembed
In part four of the RMF Categorization podcast series, the SMEs discuss the various roles and responsibilities as well as the operating environment. Any individual that interacts with a system has a certain role or responsibility in the implementation of the system security program. These roles and responsibilities are propagated across three tiers: 1) the organization, 2) mission/business processes and 3) information systems. The operating environment consists of the system authorization boundary as well as all external entities interacting with the system information types. The operating environment should result in a specific implementation of prescribed security requirements and provide a measurement of a security program’s effectiveness.
https://www.youtube.com/embed/EU9YHjanK0o?feature=oembed