Are you interested in delivering a webinar presentation on your DoD research and engineering efforts?
CSIAC hosts live online technical presentations featuring a DoD research and engineering topic within our technical focus areas.
Host a Webinar with CSIAC
Upcoming Webinars
AI Reliability Risk Assessment
Reliability of a military system refers to its ability to complete a specific mission without failure. Failure modes in traditional acquisition systems often involve hardware, software, and human-systems integration. These failure modes are generally well-understood…
Past Webinars
A Multilayered Defense Strategy Against Adversarial AI Attack
In the digital era, the cybersecurity landscape faces an unprecedented challenge from adversarial attacks, which manipulate data and machine-learning (ML) algorithms to undermine security systems….
Responsible Artificial Intelligence (RAI) Toolkit DAGR and SHIELD
The Responsible Artificial Intelligence (RAI) Toolkit provides a voluntary process to identify, track, and improve alignment of AI projects to RAI best practices and the…
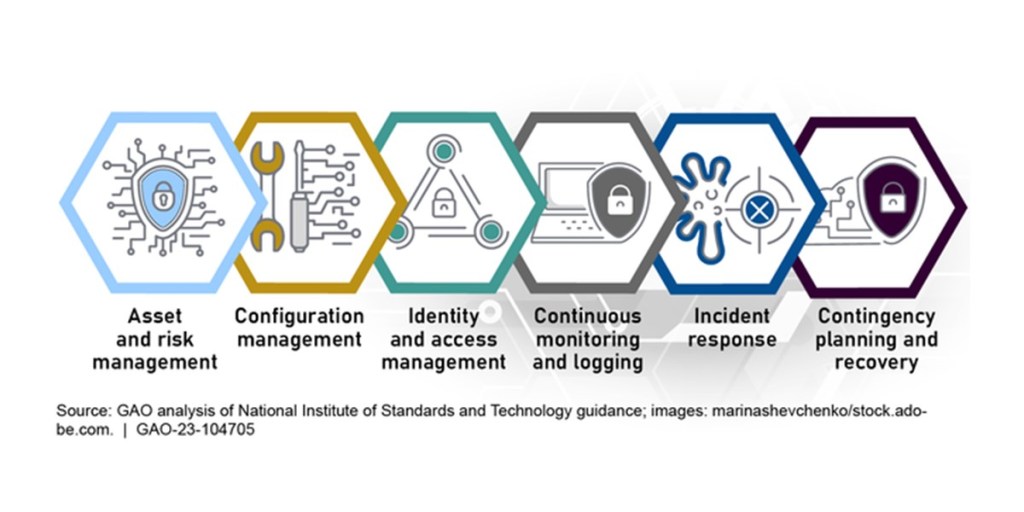
Government Accountability Office’s Cybersecurity Program Audit Guide (CPAG)
This presentation will focus on the origin of the CPAG and how individuals and auditors can use it when planning for and conducting cybersecurity-related performance…
Do I Need Cybersecurity Maturity Model Certification (CMMC) and Why?
On November 2010, President Obama issued Executive Order 13556 that formed the controlled unclassified information (CUI) program. Six years later, the Defense Federal Acquisition Regulation…
Research Challenges for Large Pretrained Models
This webinar will highlight research challenges cutting across U.S. Army, Navy, and Air Force use cases for large pretrained models to include research on the…
Improving Security, Privacy, and Authentication With a Quantum-Enhanced TCP/IP Protocol
Secure communications need to exchange encryption keys over encrypted channels often implemented with asymmetric algorithms. Because both the session key transmission and digital signatures use…