Are you interested in delivering a webinar presentation on your DoD research and engineering efforts?
CSIAC hosts live online technical presentations featuring a DoD research and engineering topic within our technical focus areas.
Host a Webinar with CSIAC
Upcoming Webinars
Deceptive AI: Understanding and Defending Against the Next Generation of Cyber Weapons
COMING SOON – EXACT DATE AND TIME TBD. In the evolving theater of modern warfare, artificial intelligence (AI) has emerged as a transformative force and new frontier of vulnerabilities. This presentation provides a critical analysis of…
Past Webinars
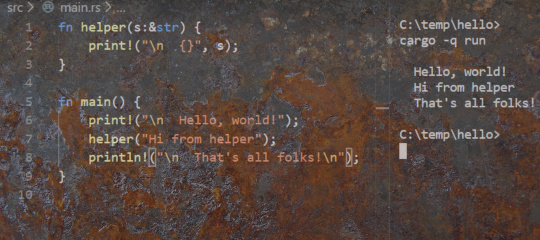
Rust Error Handling
Rust is a modern programming language that supports safe system programming with: compiler verified freedom from undefined behavior, support for building race-free multithreaded code, and…
USAF Software Assurance (SwA) Training Approach
Hiring has always been a challenge, but the unique workload of software avionics, hardware integration, and cyber resiliency produce a unique situation that the U.S…
Beyond the CIA Triad
In this CSIAC podcast, Jim West discusses how the CIA triad has played a part in the management of risk, but lacks the details of…
Security Engineering Risk Analysis (SERA): Connecting Technology Risk To Mission Impact
The Security Engineering Risk Analysis (SERA) Method defines a systematic approach for evaluating cybersecurity risk in highly complex networked environments. The SERA Method uses a…
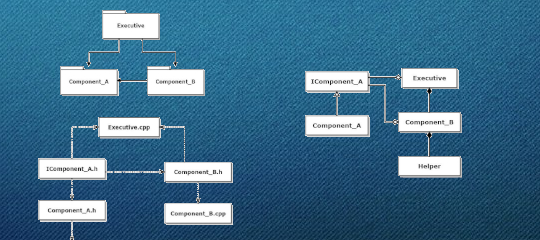
Code Structure – C++ Models Part 1 -6
This is a 6-part video series entitled C++ Models by Dr. James Fawcett. Each video describes different conceptual models underlying the C++ programming language. Discussion…
NREL’s Energy Security and Resilience Center
This webinar discusses the National Renewable Energy Laboratory’s ongoing work to ensure energy security and resilience in today’s interconnected and interdependent world. Today, widely available…