The CMMC framework builds upon existing regulations like National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 but introduces a certification requirement to validate compliance. CMMC applies to any organization in the DoD supply chain and helps protect against cyberthreats by enforcing stricter cybersecurity controls.
CMMC consists of different levels that define the cybersecurity maturity of an organization:
Level 1 (Foundational)
- Who It Applies to: Companies that handle FCI but not CUI [2].
- Requirements: Must implement 17 basic cybersecurity practices aligned with Federal Acquisition Regulation (FAR) 52.204-21 (“Basic Safeguarding of Covered Contractor Information Systems”).
- Assessment: Annual self-assessment (no third-party audit required).
Level 2 (Advanced)
- Who It Applies to: Companies that process, store, or transmit CUI.
- Requirements: Must comply with NIST SP 800-171, which includes 110 cybersecurity controls for protecting CUI.
- Assessment: Prioritized programs (critical national security), which require a triennial certified third-party assessment organization (C3PAO) audit; nonprioritized programs require an annual self-assessment.
Level 3 (Expert)
- Who It Applies to: Companies working on the most sensitive DoD contracts involving CUI with heightened security risks.
- Requirements: Must comply with NIST SP 800-171, plus additional security controls from NIST SP 800-172 for advanced threat protection.
- Assessment: Triennial government-led assessment conducted by Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
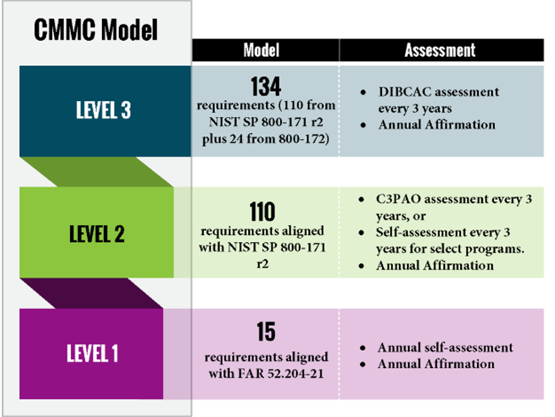
Figure 1. Diagram of the Three Levels Found in the CMMC Model (Source: DoD Chief Information Officer [CIO]).


