Types of DDoS Attacks
-
Volumetric Attacks: Send a high volume of traffic to a specific target to consume its bandwidth and impede the victim’s internet access [2].
-
Application Attacks: Intentionally exhaust server resources by sending an overwhelming amount of hypertext transfer protocol (HTTP) requests to a server during a short amount of time, which can compromise the functionality of an application. Each HTTP request asks for the server to load a webpage, which consumes resources on the server side. These are also referred to as “Layer 7 attacks” due to the DDoS targeting the seventh layer of the Open Systems Interconnection (known as OSI) model.
-
Protocol Attacks: Disrupt communication within a network by exploiting vulnerable network protocols, hindering the communication between devices and the server.
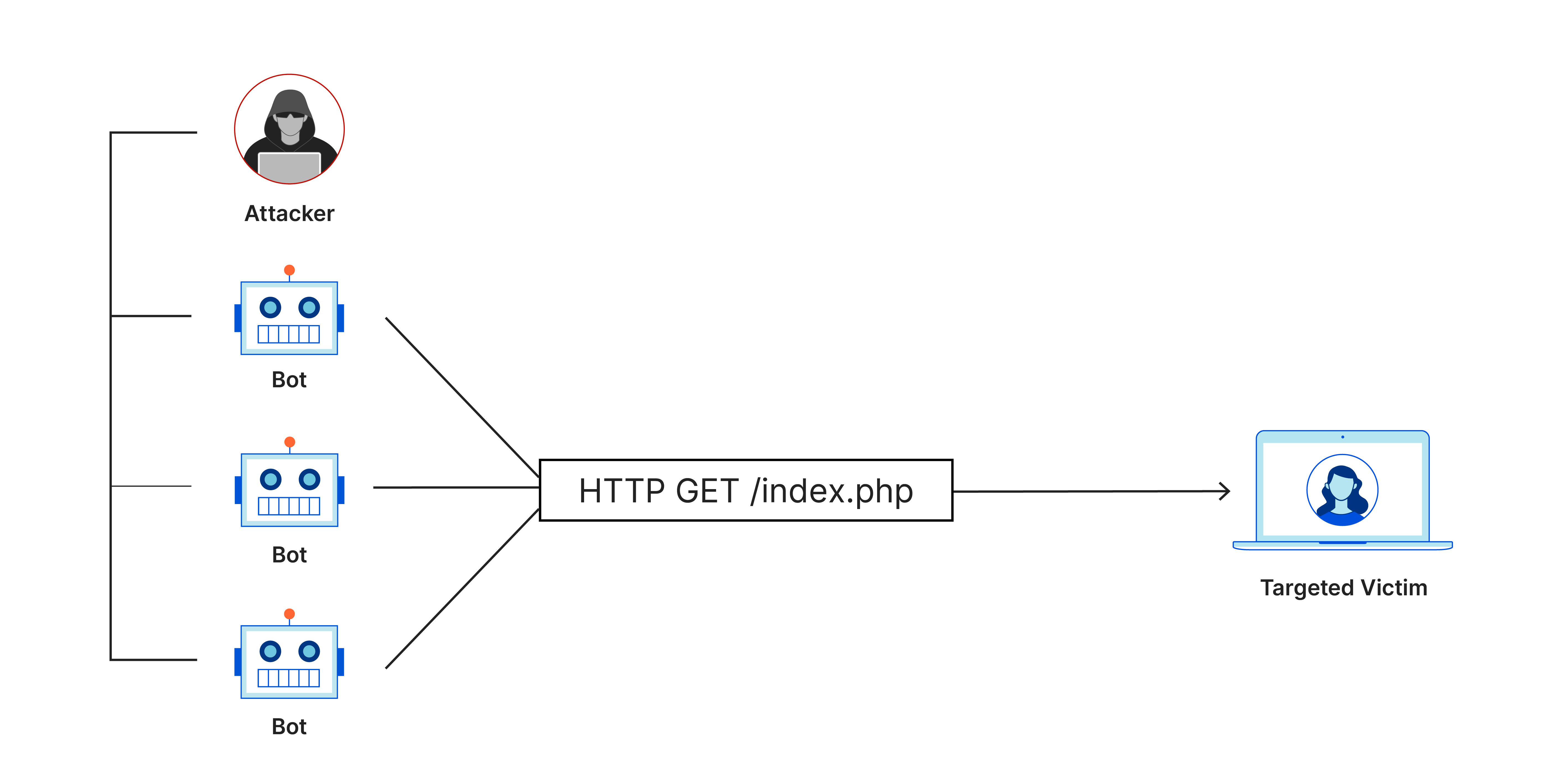
Figure 1. Diagram of Main Elements Present in a Typical DDoS Attack (Source: Cloudflare).
Preventing DDoS Attacks
Preventing DDoS attacks can be crucial in ensuring that critical networks remain operational and accessible [3]. There are several security practices and tools used to protect against these cyberattacks, which include the following:
-
Rate Limiting: Restricting the number of requests that can be received by a single user over a certain duration. This prevents servers from getting overloaded with traffic from a specific malicious source.
-
Attack Surface Reduction: Implementing restrictions on which users can access a server, depending on their location, network settings, and applications used.
-
Threat Monitoring: Observing live website traffic to spot any anomalies that could be a sign of a DDoS attack and acting based on the information.
-
Other DDoS Prevention Tools
-
Web Application Firewall
-
Intrusion Detection/Prevention Systems
-
DDoS Mitigation Software
-
Content Delivery Networks (CDNs)
-
Traffic-Scrubbing Services
-
Notable DDoS Attacks
Google Cloud (2023)
Google Cloud was the victim of the largest DDoS attack recorded in history, with its servers receiving a record-breaking 398 million requests per second (RPS) [4]. This attack was 7 1/2 times larger than the previous largest attack, which peaked at 46 million RPS. Google was able to block the attack, which used a new “Rapid Reset” technique to send a high amount of HTTP requests.
U.S. States and Airports (2022)
A Russian hacking group, known as “Killnet,” was able to take down over a dozen state government websites in an orchestrated DDoS attack [5]. The websites remained inaccessible to users for an extended time, disrupting critical infrastructure and services. Shortly after the initial attack, the group launched another DDoS attack targeting around 40 major U.S. airports, causing their websites to go offline by sending a large amount of malicious traffic.
Amazon Web Services (2020)
Amazon received a DDoS attack, with traffic peaking at 2.3 TB/s. The hacker was able to exploit a network protocol called Connectionless Lightweight Directory Access Protocol (known as CLDAP), which is a protocol used for user directories.


