Accelerating Cyber Resilience: Air Force, DARPA Join Forces to Strengthen Cyber Defenses
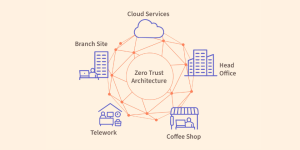
A strong, lethal military demands cutting-edge and resilient software to power every weapon and support system our U.S. Warfighters depend on. However, the U.S. Department of Defense’s (DoD’s) reliance on aging IT infrastructure, using security policies developed over the last 30 years, creates inherent vulnerabilities in its systems, from legacy architectures to advanced weapons. Meanwhile,…