Introduction
As satellites become increasingly integral to global communication, navigation, and surveillance, targeting their vulnerabilities by malicious actors to disrupt services or gain sensitive information will be imminent to maintain cyberspace security.
Cybersecurity in cyberspace is a versatile field dedicated to safeguarding digital information and infrastructure from a spectrum of cyberthreats and attacks. Cyberspace focuses on protecting the integrity, confidentiality, and availability of satellite systems and their associated data from cyberthreats and attacks.
The importance of cybersecurity controls regarding cyberspace includes robust encryption protocols, secure communication channels, regular system updates, and comprehensive threat monitoring to mitigate risks.
This article will focus on low Earth orbit (LEO), acknowledge medium Earth orbit (MEO) and geostationary Earth orbit (GEO), and discuss the main differences between them (Figure 1).
![Figure 1. Classification of Satellite Orbits (Source: Saliby [1]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-1.jpg)
Figure 1. Classification of Satellite Orbits (Source: Saliby [1]).
Exploring Various Types of Orbits
An orbit is the curved path that an object like a satellite in space takes around another object due to gravity. In space, there is no air and, therefore, no air friction. Because of this, gravity lets the satellite orbit around Earth with almost no further assistance [2].
For cybersecurity specialists, there will be some requirements to understand the basic terminologies regarding satellites’ cyber safety and exploring their orbits, as the future of this country and its security depend on it.
As of July 2024, there were 6,281 Starlink satellites in orbit, with a potential to reach 42,000 satellites forming a mega constellation [3] (Figure 2).
![Figure 2. Starlink V2 Satellites Launched From Space Launch Complex 40 (SLC-40) at Cape Canaveral Space Force Station in Florida (Source: Langbroek [4]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-2.jpg)
Figure 2. Starlink V2 Satellites Launched From Space Launch Complex 40 (SLC-40) at Cape Canaveral Space Force Station in Florida (Source: Langbroek [4]).
LEO
LEOs will be the most accessible part of space for a broad range of operators. Even Amazon Web Services and Microsoft’s Azure now provide Ground Station as a Service to enable communication with LEO satellites. LEO will initially host most space-based computing devices, which will require robust cybersecurity measures and controls, making them a primary target for adversaries.
Any space object that exists in an orbit below an altitude of 2,000 km above Earth is considered a LEO (Figure 1). A popular type of LEO satellites is known as “SmallSats,” meaning small satellites [5]. Due to their proximity to Earth, these satellites are extensively utilized for a variety of applications, including telecommunications, Earth observation, and scientific research, leveraging their advantageous low-latency characteristics and enhanced resolution capabilities.
LEOs come in the following wide range of sizes and masses:
- Minisatellite: 100–180 kg
- Microsatellite: 10–100 kg
- Nanosatellite: 1–10 kg
- Picosatellite: 0.01–1 kg
- Femtosatellite: 0.001–0.01 kg
LEO SmallSats’ cybersecurity controls are characterized as CubeSats. They are measured by units of U’s, where 1U is the equivalent of 10 × 10 × 10 cm [6].
MEO
MEO satellites are higher than the 2,000-km altitude and lower than the GEO satellites. They are primarily recognized for supporting regional coverage in global navigation satellite systems. A historical analysis of the progression of these satellites will provide a more nuanced and thorough understanding of their developing and current capabilities.
The United States initiated the deployment of its Global Positioning System (GPS) in early 1978, with the individual satellites designated as Navstar. It was not until 1982 that the Soviet Union launched its own counterpart, the Global Navigation Satellite System (GLONASS). The Chinese system, known as Beidou (meaning “compass”) was introduced later, with its first satellite launched in 2007 [7].
While MEO satellites compare in size to a standard refrigerator or a small car, the size of GEO satellites has significantly evolved since their inception, expanding from a mere few hundred kilograms to over six metric tons today.
GEO
GEO satellites typically range in size from about 1,000 kg (2,200 lb) to over 6,000 kg (13,200 lb) [8]. Their dimensions can vary widely, with some being as large as a car and others as large as a bus. Generally, they have large solar arrays and antennas, which can extend their overall size drastically.
Why Altitude Matters
Satellites traverse earth’s orbit due to the intricate equilibrium between gravitational forces and their orbital velocity. Upon launch, a satellite reaches a precise velocity that permits it to perpetually descend toward Earth while advancing forward, thereby achieving a stable orbit.
Since SmallSats are within a certain altitude, they orbit Earth every 60 to 90 min. While MEOs orbit Earth between 8 to 15 hr, GEOs take 24 hr to orbit.
The higher a satellite orbit, the slower it moves. Since GEOs are equatorial orbits, they will be above the same spot over Earth at all times. This is extremely important, as it impacts the windows of communication with ground stations.
SmallSats orbit earth every 90 min, and the window in which they will be visible to their ground stations is only a few minutes. Because they are so close to Earth, they do not consume much energy to get their communication signals to the ground stations or receive instruction commands or a payload patching a vulnerability in their software [9].
The Cyberspace Challenge
When it comes to cyberattacks within cyberspace, there is always a motive and an intention.
Intention denotes the specific plan or goal an individual or a group aims to achieve with their actions, whereas motive encompasses the underlying reasons or drives that inspire those actions. Intentions are typically conscious, while motives can operate at both conscious and subconscious levels.
The cyber risk analysis regarding satellite systems is based on intention and motivation of threat actors and determination of the impact and probability of success undermining the satellite integrity and/or availability. The type of missions conducted by the targeted satellite will dictate the most effective vectors for cyber activity and the subsystems most susceptible to exploitation. These incorporated satellite mission types could be remote sensing or emitting types [10].
Regularly referred to as Earth observation satellites, sensing satellites are specialized satellites designed to collect data regarding the Earth’s surface and atmosphere. Sensing is through electromagnetic spectrum sensors, radio waves, infrared radiation, and visible light, which are the same types of data commonly used in internet-based mapping applications or for weather forecasting and meteorological analysis and oceanography.
Emitting satellites are crucial for global communication systems and designed to transmit signals, data, or broadcasts back to Earth or to other satellites. These satellites facilitate the transmission of signals for satellite television services and help provide broadband connectivity to remote areas.
Emitting could also be used in overt or covert operations. Jamming or blocking signals is a classic example of an overt operation targeting other satellites’ sensors and performing a communication takeover. Covert operations like spoofing signals are similar to what is seen in electronic warfare.
Defending the Kármán Line
In cybersecurity, one of the most popular and effective cyber defense architectures is defence-in-depth (Figure 3), where there is perimeter security. Imagine this perimeter security is the Kármán line, which is the line used for regulatory purposes to differentiate between aircraft and spacecraft spreading a boundary 62 miles or 100 km above mean sea level that borders Earth’s atmosphere and the beginning of space [11].
![Figure 3. Defence-in-Depth Cybersecurity (Source: Saliby [1]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-3.png)
Figure 3. Defence-in-Depth Cybersecurity (Source: Saliby [1]).
The simplest example of a space system involves a ground-based station device communicating with a space-based device “satellite” where both devices transmit and receive signals (Figure 4).
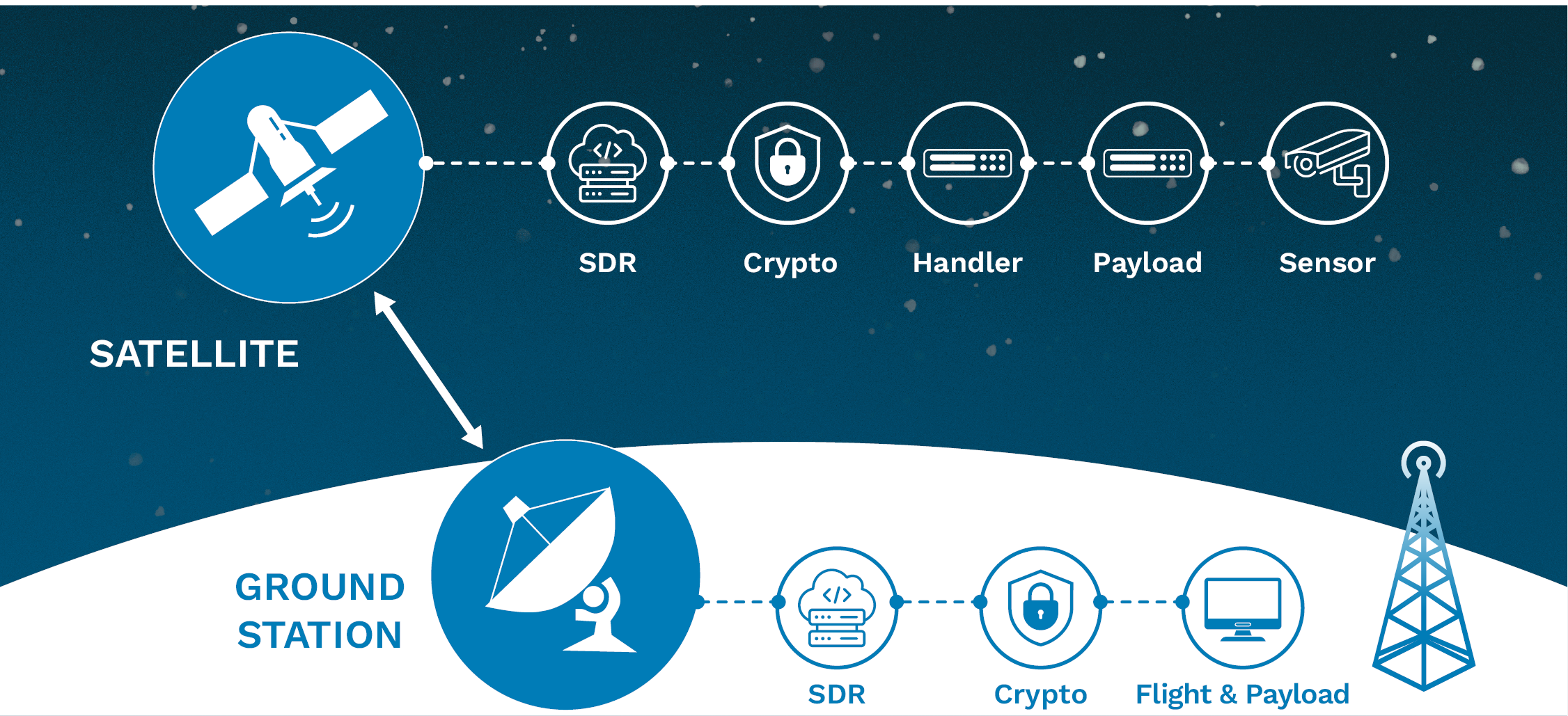
Figure 4. Satellite Communications Relay (Source: Canva).
On the ground-base station, a software-defined radio (SDR) is responsible for receiving various signals like modulation, demodulation, filtering, and encoding and turning them into communications. Providing decryption of the communications stream passes it to a flight control computer running the software that communicates and controls the satellite used for keeping track of its flight operation and trajectory. This provides greater versatility and efficiency in modern communication systems and electronic warfare [6].
An attacker with access to one or more satellites could potentially redirect these satellites to receive commands not only from the legitimate ground station but also from attacker-controlled ones. By configuring a compromised satellite to listen for and accept instructions from a rogue ground station, the threat actor would undermine the integrity of the communication system.
SDRs enable cyberattacks to compromise communications either from the ground or the satellite. Both ground stations and space vehicles commonly use SDRs to configure, transmit, and receive signals through their antennas. An attacker could exploit vulnerabilities in these SDRs to disrupt communication streams, either by altering configurations or introducing gradual subtle degradation. This kind of attack might not result in an immediate communication shutdown that triggers a rapid response from operators. Instead, it could cause intermittent and unreliable communication between ground and space systems. Consequently, operators might redirect communications to alternative ground stations, affecting the coverage and effectiveness of the space vehicle or its network.
Inadequately implemented encryption jeopardizes confidentiality and creates a misleading sense of privacy and security for the communicating parties. This illusion of protection persists until the parties discover that the secure encryption has been compromised.
Ground-to-space communications encounter augmented risks pertaining to the resilience of encryption. Unlike wired or other mediums, these communications are continuously transmitted through air, making them susceptible to interception. Even though the data is encrypted, the constant and extensive transmission exposes the encryption to potential analysis. An attacker might exploit these frequent and large communication sessions to detect patterns and potentially break the encryption.
Cyberspace Mitigations and Controls
There are many safeguards and controls already incorporated in most satellites. These controls focus on redundancy, with some resilience embedded into their architecture.
A recent analysis conducted by a team of German researchers offers an insightful examination of the security vulnerabilities present in satellites currently orbiting Earth [12]. The researchers, affiliated with Ruhr University Bochum and the Cispa Helmholtz Center for Information Security, scrutinized the software utilized by three small satellites and discovered significant deficiencies in basic protective measures. According to their findings, the satellites assessed exhibited vulnerabilities within their firmware, revealing that minimal security advancements from the past decade have permeated the space domain.
Notably, these satellites lack adequate safeguards concerning who can communicate with their systems and do not incorporate encryption protocols. The researchers suggested that such shortcomings could allow an adversary to seize control of a satellite, posing risks of collision with other objects.
The analysis identified six distinct types of security vulnerabilities across the three satellites, totaling 13 vulnerabilities. Among these are “unprotected telecommand interfaces,” which are critical for satellite operators on the ground to communicate with the spacecraft in orbit.
SmallSats and CubeSats
These nanosatellites exhibit heightened vulnerabilities to cyberattacks due to their low construction costs for commercial entities. The proliferation of thousands of satellites in constellations congests LEO, creating fertile ground for malicious actors, especially in conjunction with military satellite deployments. Compromising these satellites could lead to significant economic ramifications and even potential loss of lives.
For instance, by compromising the satellite’s navigation system, an attacker could cause failure in its docking maneuvers or alter its orbital trajectory, potentially redirecting it to face Earth rather than the Sun. This will be explored in the “RoSat Attack” section of this article.
Private Sector and Field-Programmable Gate Arrays (FPGAs)
The private sector has largely neglected cybersecurity, possibly due to a lack of awareness and compounded by the financial burden of adequately securing satellites against cyberthreats and the absence of regulatory frameworks.
Implementing advanced encryption methods like quantum encryption could substantially fortify the cybersecurity of satellites against these threats, coupled with deploying secure gateways reinforced by intrusion prevention systems.
While FPGAs are useful for monitoring systems and overseeing the logic necessary to keep them running with minimal interruption when individual components fail, a complete microcontroller watchdog with logic for failure handling can be implemented in a hardware description language [13]. Invoking or triggering the watchdog scripts or watchdog timer (WDT) by various situations will correct an error in navigation after a certain threshold.
WDT
A WDT is a system monitoring mechanism designed to detect and respond to failures or malfunctions in satellite software or hardware; it could be a lifesaver for SmallSats. The WDT operates by resetting at regular intervals, requiring the system to reset within a specified timeframe to prevent errors or crashes. If threat actors were to disrupt the GPS system from a ground station, a WDT might eventually take over the navigation system, allowing the space system operators to regain control of the space vehicle.
Gold Image
Use of a gold image is another control used in a LEO satellite’s cyber arsenal. This image is a preconfigured, standardized snapshot of an operating system with all necessary software and configuration stored onboard the satellite and used in case of a devastating error or failure [14].
Resource Limits
Resource limits are predefined, hard-coded values embedded in the satellite operating system that help to ensure the system’s ongoing functionality and extend its operational lifespan. They are predefined thresholds placed on various system resources, such as central processing unit usage, or memory allocation to prevent any single process from consuming excessive resources.
All these cyber controls help protect SmallSats from one of the most dangerous attack types—deorbit [15]. By design, all LEOs are equipped to deorbit and burn up in the atmosphere after a certain number of years. This keeps the amount of space junk floating down. For example, the Starlink satellite’s lifespan is approximately five years, in which after that it is programmed to deorbit and burn [2].
A threat actor would alter LEOs configuration to manipulate the system to either falsely indicate that the requirements for deorbiting have already been met or modifying the requirements so that deorbit is triggered prematurely based on the new configuration.
Space Attack Research and Tactic Analysis (SPARTA)
SPARTA is one threat mitigation framework for space attacks. While the SPARTA matrix framework is used to illustrate some examples, there are also several other key initiatives and agencies focused on cyberspace security, including the Space Information Sharing and Analysis Center, the Defense Advanced Research Projects Agency, and the European Space Agency (ESA).
Addressing the information and communication barriers that hinder the identification and sharing of space-system tactic, techniques, and procedures, SPARTA provides unclassified information to space professionals about how spacecraft may be compromised via cyber and traditional counterspace means (Figure 5). The matrix defines and categorizes commonly identified activities that contribute to spacecraft compromises [16].
![Figure 5. SPARTA Tactics and Techniques Matrix (Source: Saliby [1]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-5-2.png)
Figure 5. SPARTA Tactics and Techniques Matrix (Source: Saliby [1]).
For example, the “Initial Access” for the “Compromise Ground System” technique is comprised of two subtechniques: “Compromising On-Orbit Update” and “Malicious Commanding via Valid GS” (Figure 6).
![Figure 6. Initial Access Tactic - Compromised Ground System Technique (Source: Saliby [1]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-6.jpg)
Figure 6. Initial Access Tactic – Compromised Ground System Technique (Source: Saliby [1]).
Selecting Compromising On-Orbit Update
The mapping to NIST SP 800-53 Rev5, D3FEND, and ISO27001 makes it very accessible for cybersecurity teams to embed into their cyber programs and understand exactly which countermeasures they need to apply.
If these techniques (Figure 7) were applied properly, RoSat, the first cyberspace incident mentioned next, would have been easily avoided.
![Figure 7. Compromised Ground System Technique and Subtechniques (Source: SPARTA [14]).](https://csiac.dtic.mil/wp-content/uploads/2025/07/saliby-figure-7.png)
Figure 7. Compromised Ground System Technique and Subtechniques (Source: SPARTA [14]).
Cyberspace Incidents
The ability to disable or destroy satellites through cyber exploitation is no longer theoretical—it is a present and growing threat. As space-based infrastructure becomes increasingly vital for communication, navigation, surveillance, and national security, cyberattacks targeting these assets represent one of the most disruptive and potentially devastating threats of the 21st century. Such attacks can compromise sensitive data, disable critical systems, or even render entire satellite constellations inoperable, with far-reaching consequences for both civilian and military operations.
RoSat Attack
In late 1998, a joint German and U.S. X-ray sensor satellite known as Röntgensatellit (RoSat) was compromised [17]. The compromise involved a foreign threat actor gaining access to Goddard Space Flight Center using social engineering techniques, combined with an inadequately configured file transfer protocol server. The threat actor was able to access the server that contained RoSat flight mission files. Unbeknownst to the RoSat mission team, the threat actor changed values in the algorithms used by the system’s star tracker, thus making it point toward the sun and overheating. The team was able to identify the issue and correct the satellite’s positioning for what they thought was an accident, without knowing it was the result of cyber activities.
The foreign threat actor tried again months later—this time, changing the code for the altitude-control system. The satellite slewed out of control, pointing the X-ray imager toward the sun and irreparably damaging it completely [17].
Commercial Internet Service Provider Attack
On February 24, 2022, a multifaceted and deliberate cyberattack against a satellite network resulted in a partial interruption of the popular consumer-oriented satellite broadband server Viasat [18]. The cyberattack impacted several thousand customers and tens of thousands of other fixed broadband customers across Europe. Ultimately, tens of thousands of modems that were previously online and active dropped off the network.
Subsequent investigation and forensic analysis identified a ground-based network intrusion by an attacker exploiting a misconfiguration in a virtual private network appliance to gain remote access to the trusted management segment of the satellite network. The attacker moved laterally through the trusted management network to a specific network segment used to manage and operate the satellites and then used the network’s access to execute legitimate, targeted management commands on many residential modems simultaneously.
Juliana Suess, a research analyst and policy lead on space security at the defense think tank at the Royal United Services Institute, believes the cyberattack against the Viasat satellite system is a wake-up call to the space industry [12]. The European Union, United Kingdom, and United States have linked the attack to Russia, prompting the U.S. National Security Agency to speak out about satellite security.
Conclusions
Cybersecurity in LEO satellite systems presents unique challenges and opportunities due to the specific characteristics of their orbits. The cyberspace landscape for LEO satellites is multifaceted, encompassing traditional cyberthreats such as unauthorized access, data interception, and denial-of-service attacks, together with satellite-specific vulnerabilities.
A fundamental challenge in LEO cybersecurity is managing its vast satellite constellations, where the sheer volume of satellites exponentially increases the attack surface and thereby amplifies the complexity of securing its network. Each satellite represents a potential vulnerability, underscoring the need for advanced authentication protocols and stringent data integrity safeguards across the entire constellation.
There is significant future potential in incorporating physical layer security methodologies and quantum cryptography for ultrasecure communication protocols and harnessing artificial intelligence for autonomous threat detection and mitigation. However, integrating such advanced technologies must be carefully calibrated to align with the inherent limitations of satellite systems, including power consumption, payload capacity, and computational constraints. Collaborative endeavors between satellite operators, cybersecurity professionals, and international regulatory organizations are critical in formulating comprehensive standards and frameworks that safeguard these assets while promoting continued innovation.
The security of LEO satellite systems will significantly influence their viability and reliability in delivering global connectivity, making it imperative to continually evolve cybersecurity strategies in this dynamic space environment. Lessons must be drawn from past cybersecurity incidents to shape a cyberspace future that is secure and resilient.
References
- Saliby, C. “Classification of Satellite Orbits.” Infographic using Draw.io, 2024.
- ESA. “Types of Orbits.” https://www.esa.int/Enabling_Support/Space_Transportation/Types_of_orbits, accessed on 21 September 2024.
- Space.com. “Starlink Satellites: Facts, Tracking and Impact on Astronomy.” https://www.space.com/spacex-starlink-satellites.html, accessed on 13 September 2024.
- Langbroek, M. “SpaceX Starlink Objects Train.” SatTrackCam Leiden (b)log, https://sattrackcam.blogspot.com/2019/05/wowowow-spectacular-view-of-spacex.html, Screenshot, 29 May 2019.
- National Aeronautics and Space Administration (NASA). “What Are SmallSats and CubeSats?” https://www.nasa.gov/what-are-smallsats-and-cubesats, accessed on 12 September 2024.
- CubeSat. “CubeSat Design Specification.” Rev. 14.1, CP-CDS-R14.1, CubeSat Program, Cal Poly, San Luis Obispo, CA, February 2022.
- Johnson, N. L. “Medium Earth Orbits.” IAC-10-A6.4.1, NASA, 2010.
- NASA Science. “GOES Satellite Network.” https://science.nasa.gov/mission/goes/, accessed on 22 September 2024.
- Oakley, J. “Protecting the Final Frontier.” Apress, 2020.
- NASA Earth Science Data Systems. “Remote Sensing.” https://www.earthdata.nasa.gov/learn/backgrounders/remote-sensing, accessed on 20 September 2024.
- Britannica. “Kármán Line.” https://www.britannica.com/science/Karman-line, accessed on 18 September 2024.
- Wired. “Satellites Are Rife With Basic Security Flaws.” https://www.wired.com/story/satellites-basic-security-flaws/, accessed on 28 September 2024.
- Straka, B. “Implementing a Microcontroller Watchdog With a Field-Programmable Gate Array (FPGA).” KSC-2013-091, Kennedy Space Center, April 2013.
- SPARTA. “Space Attack Research and Tactic Analysis.” Countermeasure – Update Software, https://sparta.aerospace.org/countermeasures/CM0010, accessed on 18 September 2024.
- NASA. “State-of-the-Art of Small Spacecraft Technology.” https://www.nasa.gov/smallsat-institute/sst-soa/deorbit-systems/, accessed on 20 September 2024.
- SPARTA. “Space Attack Research and Tactic Analysis (SPARTA).” Matrix, https://sparta.aerospace.org, accessed on 10 September 2024.
- U.S. Naval Institute. “ASAT Goes Cyber.” https://www.usni.org/magazines/proceedings/2021/february/asat-goes-cyber, accessed on 15 September 2024.
- Viasat. “KA-SAT Network Cyber Attack Overview.” https://news.viasat.com/blog/corporate/ka-sat-network-cyber-attack-overview, accessed on 16 September 2024.
Biography
Chadi Saliby is an accredited cybersecurity architect and established cybersecurity strategist and leader who designs and engineers complex Cloud and hybrid cyber solutions to include vulnerability and attack surface exposure assessment, incident response, cyber threat hunting and intelligence, and robust security frameworks and programs. He is the director of Cloud security for the APAC region in one of the largest SaaS banking providers and a subject matter expert for CompTIA and ISC2, where he collaborates with a large team of experts and professionals to develop and prepare a new generation of cybersecurity experts. Mr. Saliby graduated from the Centre International Des Sciences Technique in business computer and programming and continued his MBA Magister en Business et Administration at Sorbonne.


