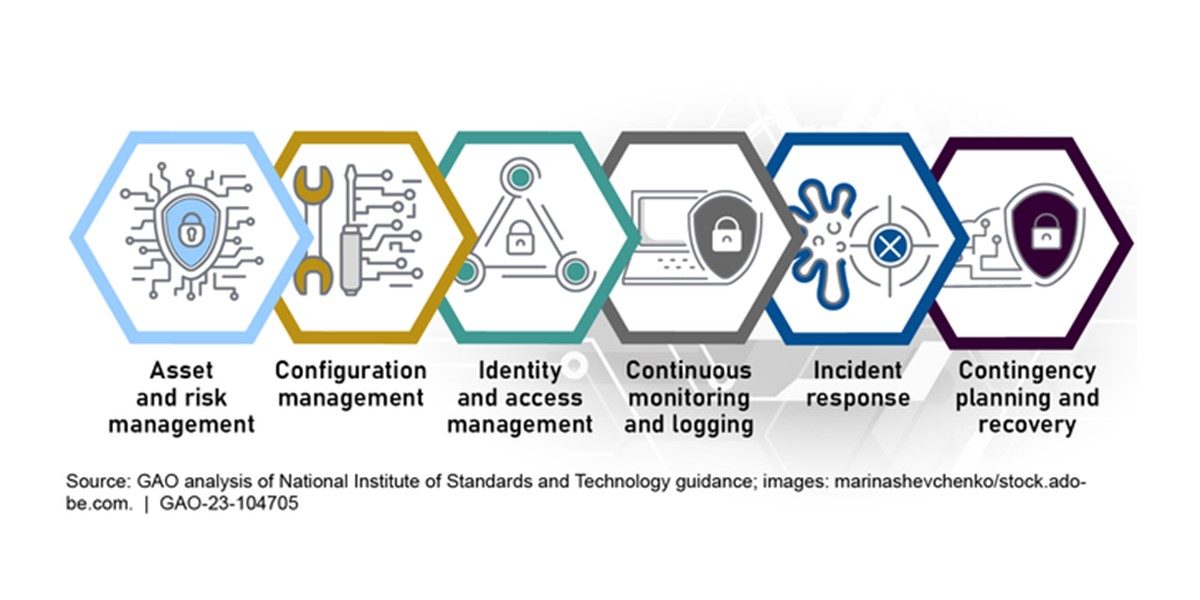
This presentation will focus on the origin of the CPAG and how individuals and auditors can use it when planning for and conducting cybersecurity-related performance audits. Attendees will gain a foundational understanding of the guide’s recommended methodologies and techniques for conducting audits and learn how they can use or tailor it to meet their specific needs. CPAG’s six primary components are as follows:
- Asset and Risk Management
- Configuration Management
- Identity and Access Management
- Continuous Monitoring and Logging
- Incident Response
- Contingency Planning and Recovery